Deploying Blue Hexagon with AWS Traffic Mirroring
Introduction
This document describes the steps needed to deploy Traffic Mirroring solution with Blue Hexagon (BH) Amazon Machine Image (AMI) and to set up integrations with AWS Security Hub and AWS Lambda. The solution described in this document utilizes many in-built features of AWS to make the deployment easier for AWS customers. For example, in this solution AWS services such as Network Load Balancer( NLB), Auto-Scaling Group (ASG) and AWS Console are used. AWS Console, for instance, is used for setting up Traffic Mirror targets and for setting up Traffic Mirror Sessions in a given AWS account.
Customers can however chose to use other solutions available from various 3rd party providers. Please note: a Blue Hexagon representative can assist you to deploy the solution.
Deployment Procedure
Here are the steps to deploy the Blue Hexagon with Amazon Traffic Mirroring.
- Blue Hexagon AMI is available as a private AMI. Therefore, customer has to provide the Blue Hexagon representative with their relevant AWS account, and region information
- Blue Hexagon will then share the BH AMI with the Customer AWS Account
- Customer can then provision the stack using the CloudFormation Template (provided via S3)
- Setup Traffic Mirror Target in their AWS console
Step-1 Information Gathering
Provide the following information to your Blue Hexagon representative:
- AWS Account ID
- VPC Region where the solution will be deployed
Step-2 Provisioning of Stack
A Blue Hexagon representative can assist you with the following steps.
- Blue Hexagon representative will provide the CloudFormation Template(CFT) (or an S3 link to the CFT) to deploy the BH Appliance Stack in the customer's account
- Before you proceed with deployment, you have to decide whether you want to provision an "SNS Topic" to be used by Blue Hexagon ASG, or the CFT will create one for you. It is preferred to create a new SNS Topic.
- Log in to your AWS Console, and switch to the region where you want to deploy the stack.
- In the AWS console, navigate to the CloudFormation page. You can search for services in the main page of the console, and click on it.
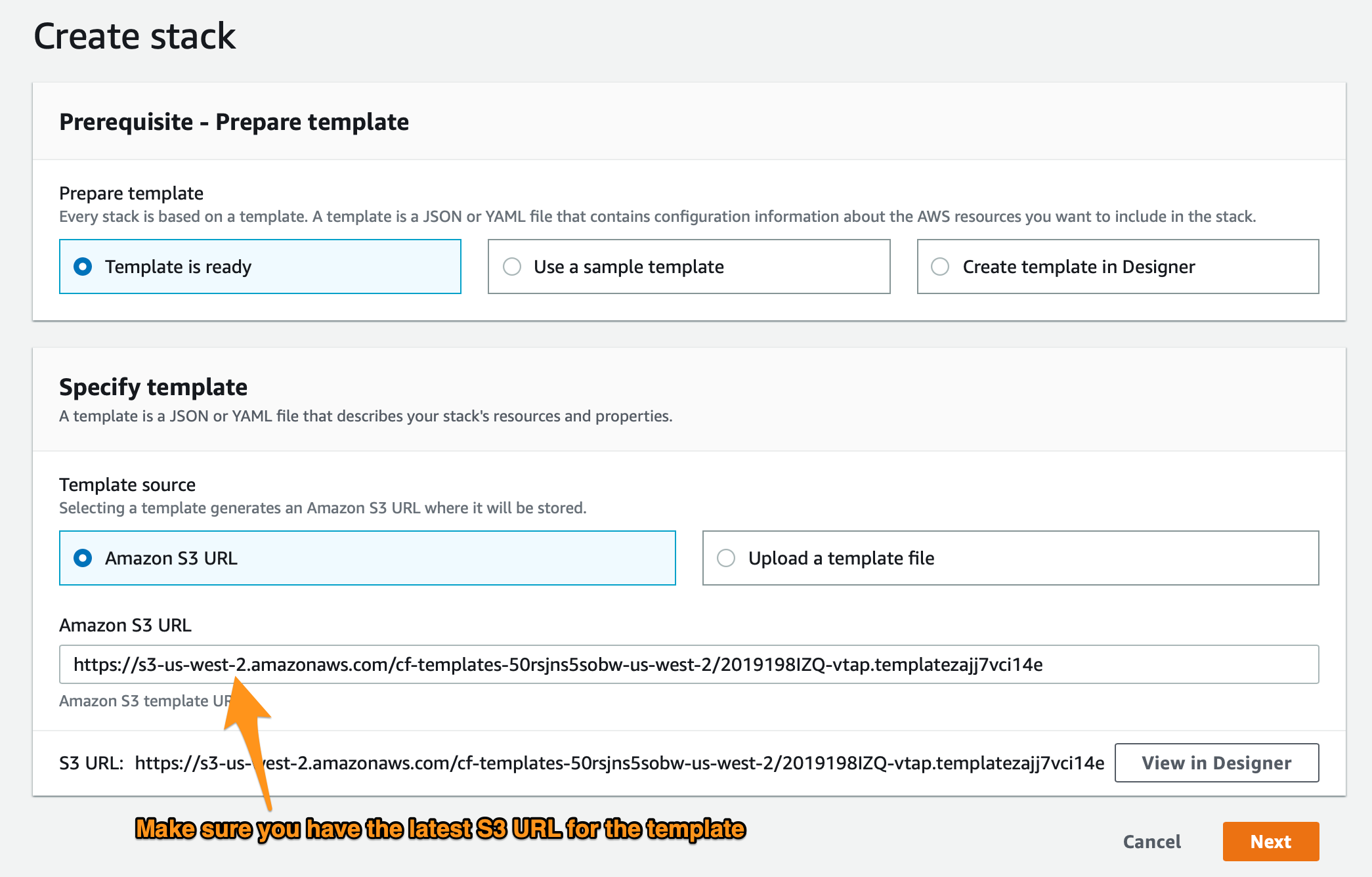
- In the CloudFormation page, click on "Create stack", and stack creation wizard enter the S3 URL you obtained in (1).
- In the Next page, a Form appears where we need to fill in the appropriate information, this includes:
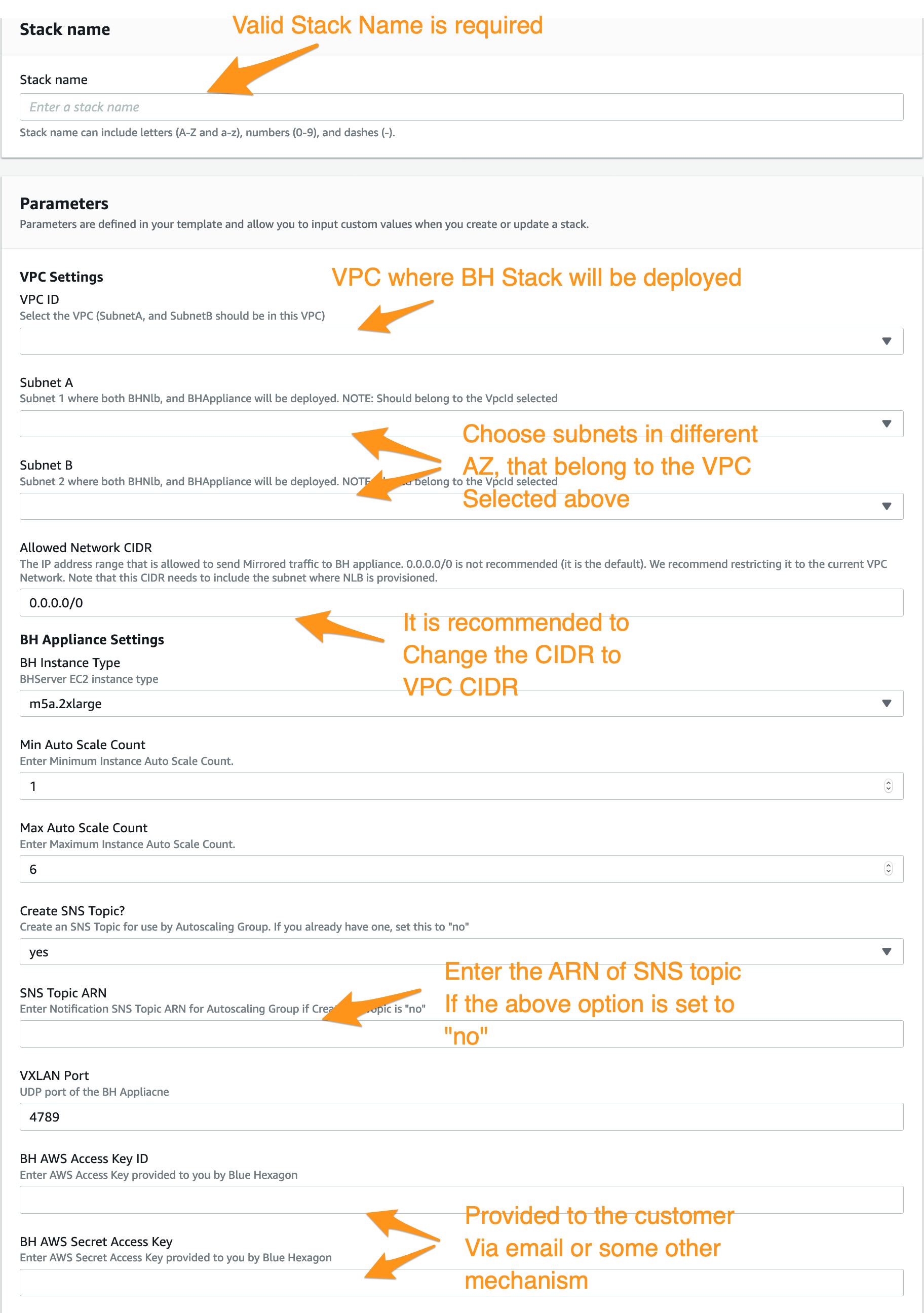
- Stack Name: A valid name is required. It can include letters (A-Z and a-z), numbers (0-9), and dashes (-).
- VPC ID: Pick the appropriate VPC from the drop-down list. The Subnets chosen above, need to belong to this VPC.
- Subnet A: This is a drop-down list of subnets in their account. Choose one that belongs to the VPC
- Subnet B: This is a drop-down list of subnets in their account. Choose one that belongs to the VPC. Note that it needs to be in an AZ different from SubnetA
- Allow Network CIDR: Default is set to 0.0.0.0/0. Should be changed to VPC CIDR.
- BH Instance Type: Default is set to m5a.2xlarge. The other available option is m5.2xlarge.
- Min Auto Scale Count: Default is set to 1. Can be increased to 2.
- Max Auto Scale Count: Default is set to 6. This can be changed, and they should not go below 2.
- SNS Topic ARN: Default is actually some junk ARN. Input the ARN of the SNS Topic provisioned in (2)
- VXLAN Port: Leave the default, which is 4789
- You can skip the Next screen, unless you want to add additional Tags or make other adjustments.
- In the final screen, accept the acknowledgement box, and click on "Create Stack"
The deployment should be done in 15 minutes.
Step-3 Setting up Traffic Mirror Target
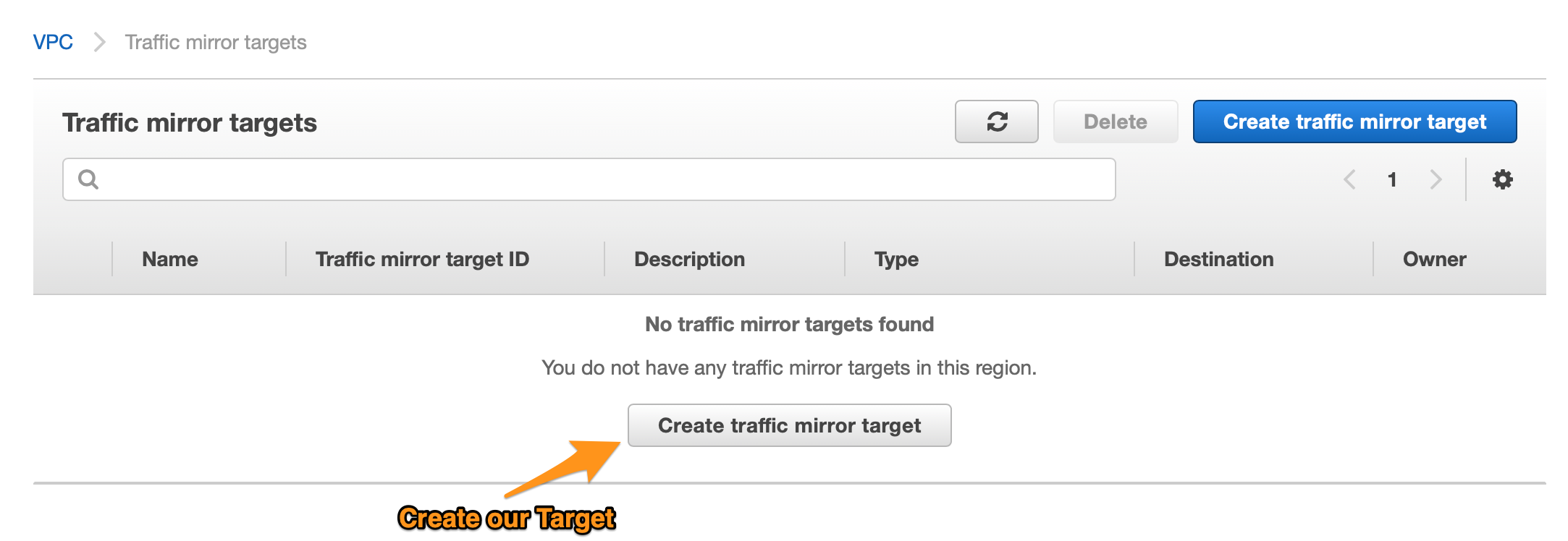
- Once Step 2 finishes, go to VPC Dashboard. Scroll all the way down, and on the left menu, click on "Mirror Targets"
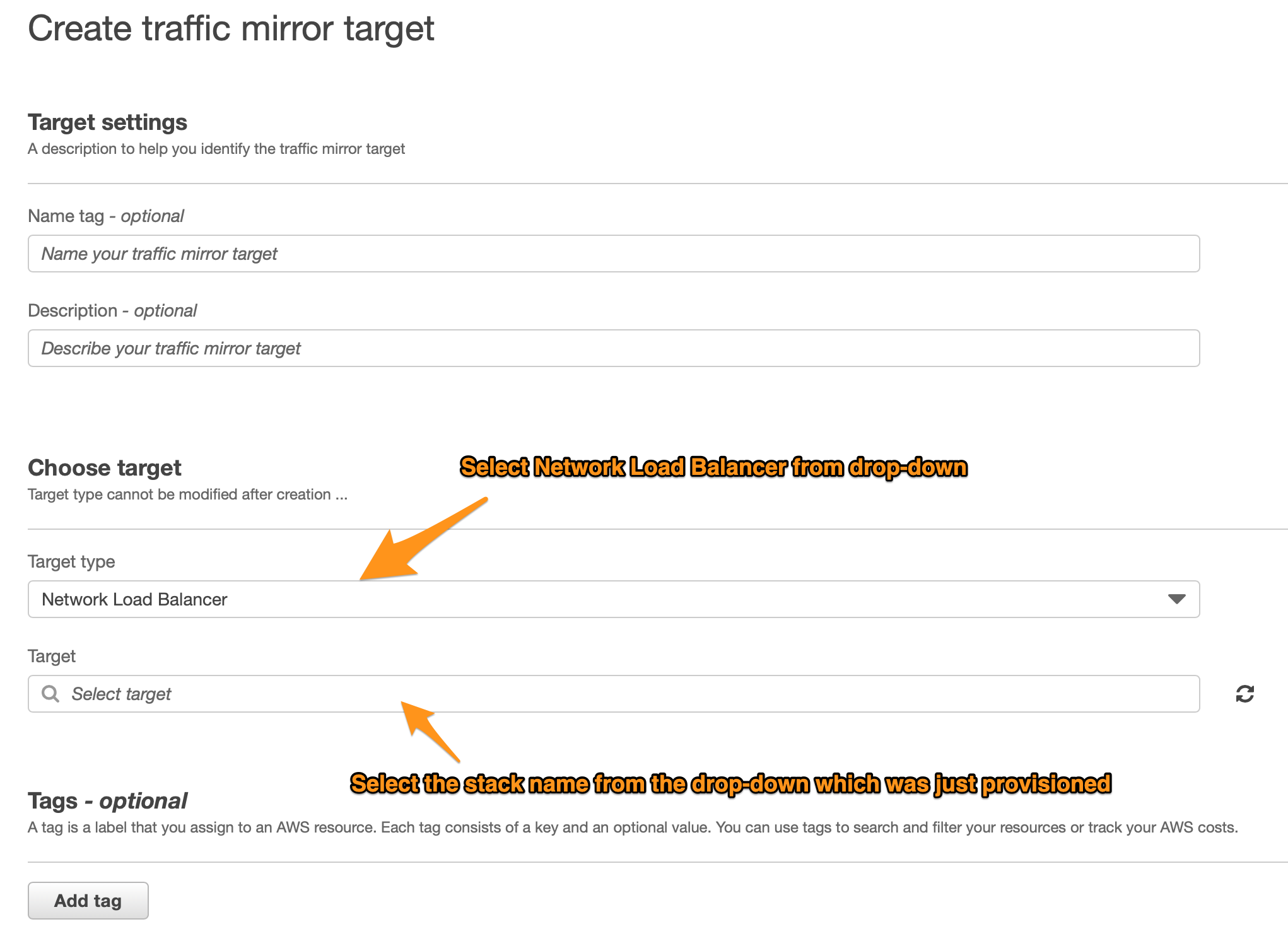
- To create a Target, choose "Network Load Balancer" from the "Target Type" drop-down list
- And now, choose the "Target", which will be the "Stack Name" used in Step-2.6.
- Other tag details is up to your discretion
Creating traffic mirror target
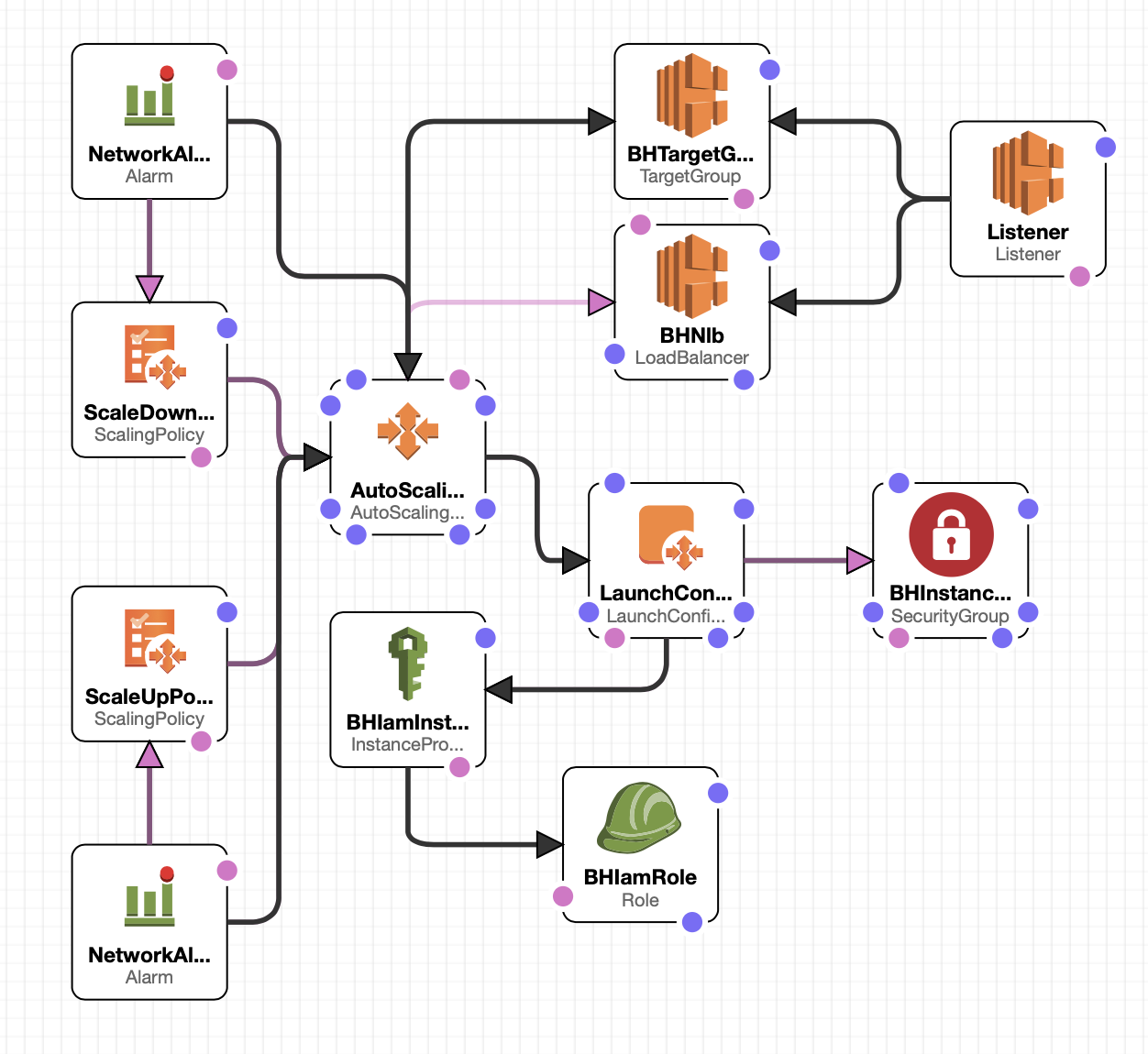
Reference Architecture
Traffic Mirroring in AWS is a virtual TAP that provides direct access to all the raw packets flowing in a VPC. This traffic will be forwarded to Blue Hexagon Virtual Appliance deployed in the customer VPC, to perform traffic analysis.
This deployment architecture involves usage of AWS Native solutions:
- Network Load Balancer
- Auto Scaling Group
- IAM Policies
- Security Groups
A logical diagram of all the components involved in the architecture is presented blow
Here are the components of the architecture presented above:
- A Network Load Balancer (NLB) is deployed in a private subnet of a VPC. The NLB will not be internet-facing.
- An Auto Scaling Group (ASG) is deployed, which is responsible for auto deployment, and scaling of the BH virtual appliance (AMI).
- Minimum of 1 instance is deployed
- Maximum is set at 6
- Running Instances are increased by 1, when Average Network Bytes In exceeds 500 MB in a 10 minute window
- Running Instances are decreased by 1, when Average Network Bytes In stays below 500 MB in a 10 minute window
- Running Instance count can never be 0
- Instances are associated with an Instance Profile, which have the following policies attached to them:
- arn:aws:iam::aws:policy/SecurityAudit
- arn:aws:iam::aws:policy/ViewOnlyAccess
- The NLB FQDN will be registered as Traffic Mirror Target.
Integrations (SecurityHub and Lambda)
Blue Hexagon can be configured to publish its findings to an AWS SNS topic in your account. A finding received on the topic triggers an AWS Lambda to either:
- forward the finding to AWS Security Hub and/or
- remediate the threat by taking actions such as stopping or quarantining the infected EC2 instance.
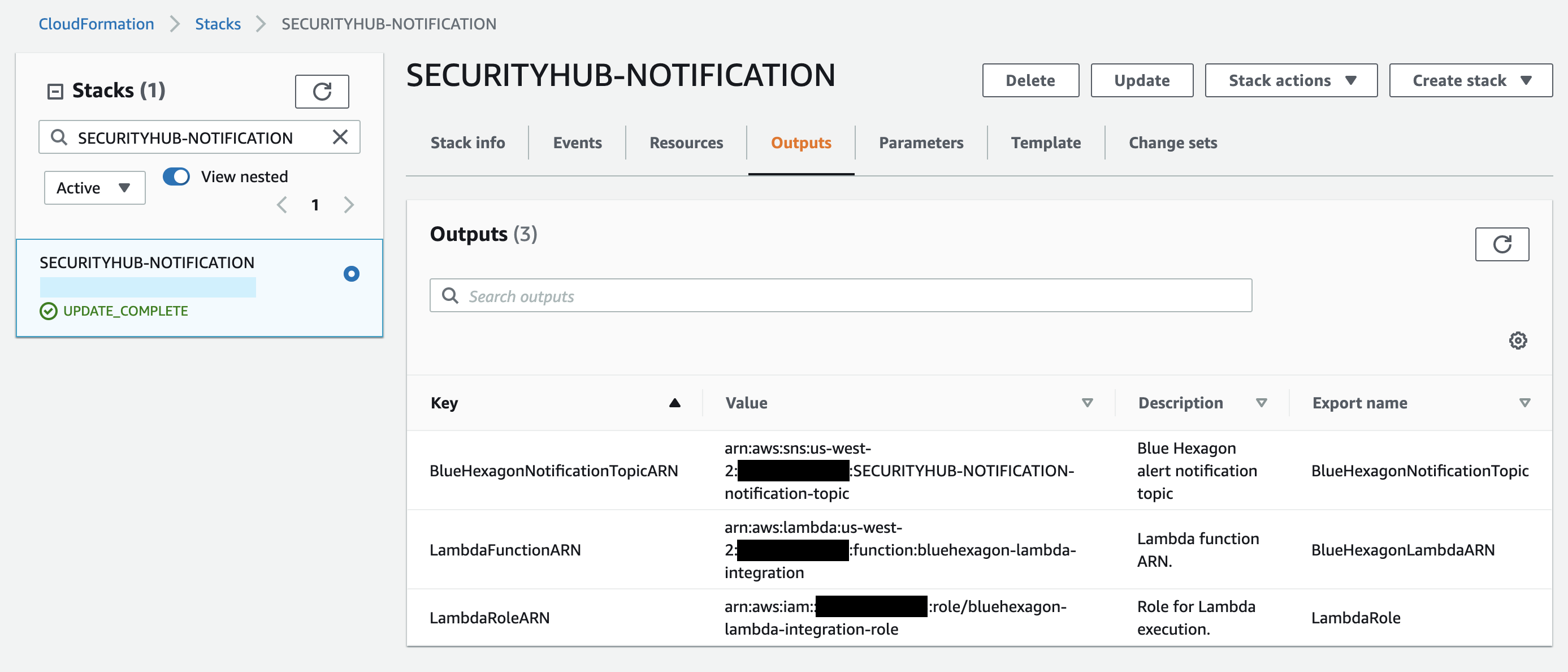
Your Blue Hexagon representative will provide the CloudFormation Template (CFT) to deploy the integrations. When deployed, the CFT creates the following resources:
- AWS SNS notification topic: All Blue Hexagon findings are published to this topic
- AWS Lambda: Adds additional context and metadata to the finding and publishes to Security Hub and/or remediates the threat
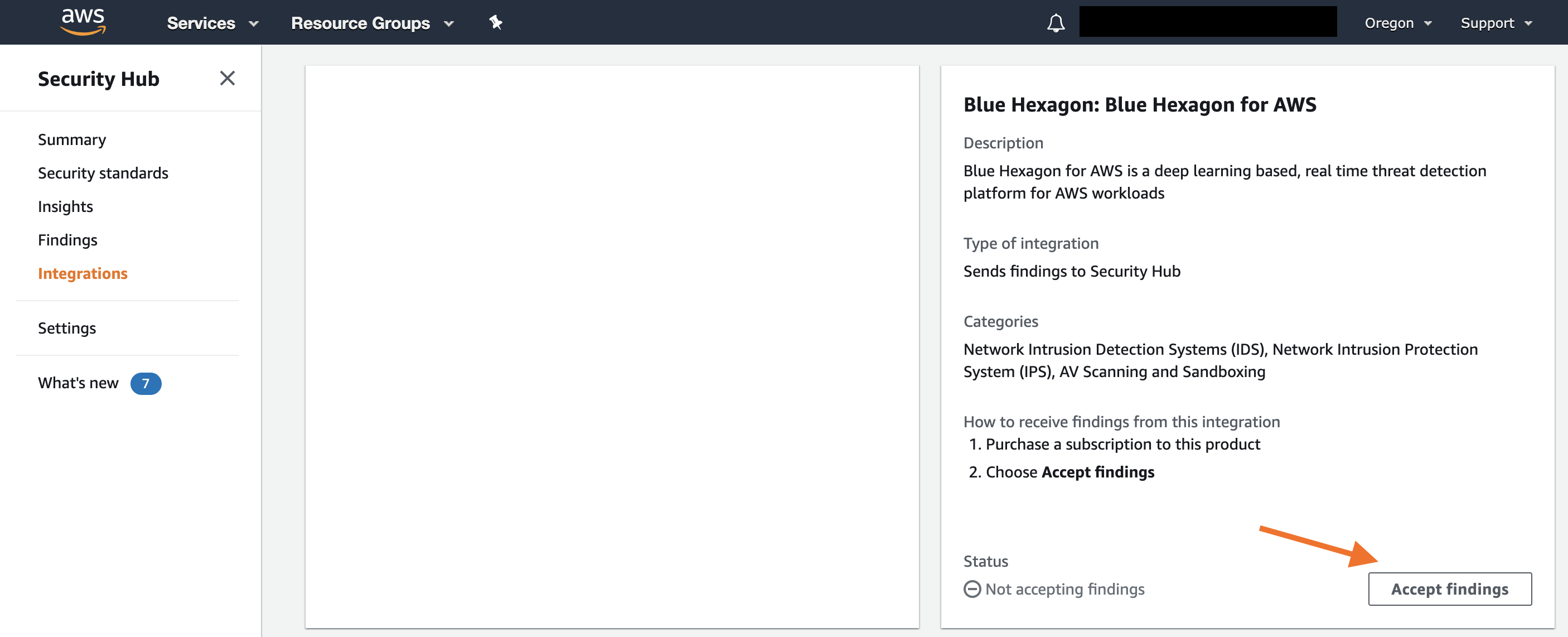
To receive findings in Security Hub from Blue Hexagon, go to the Integrations page in Security Hub and click Accept Findings.
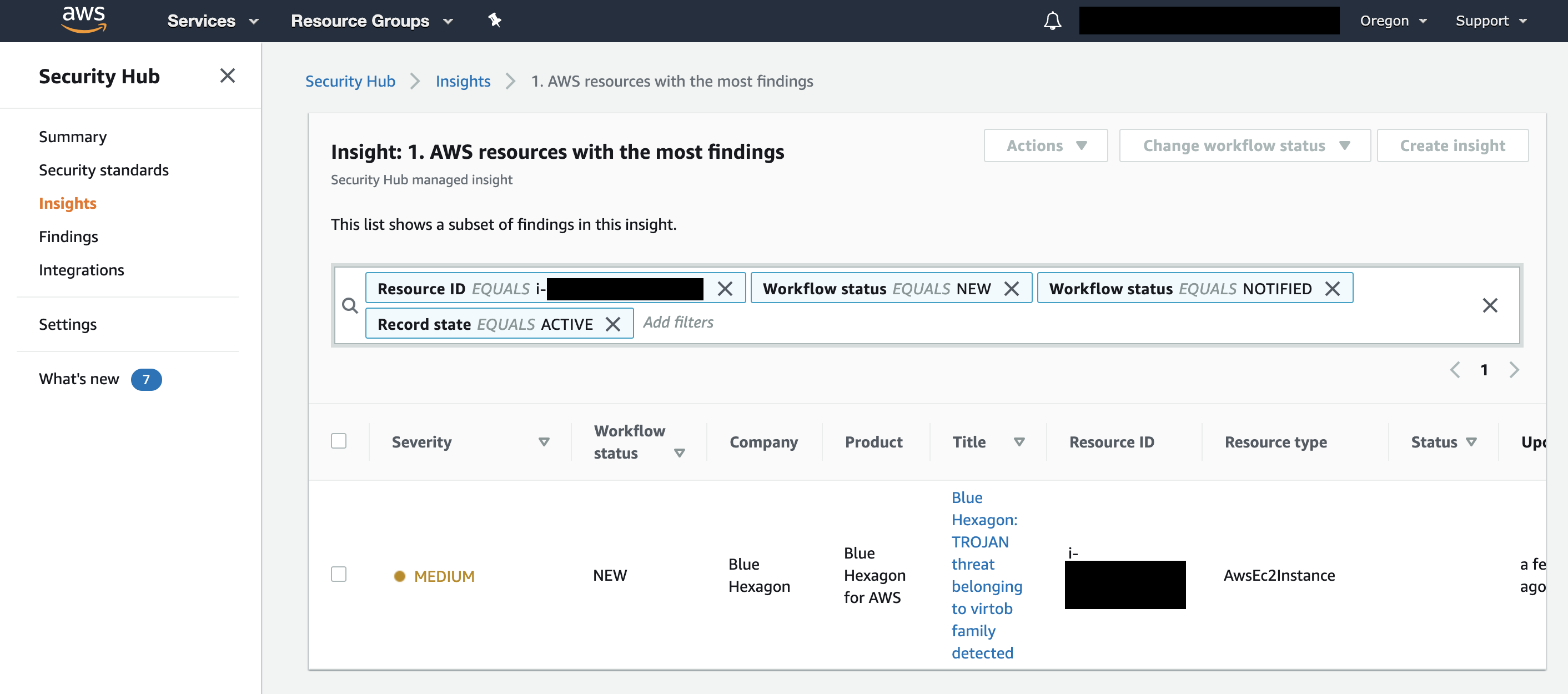
Once the integration is set up, Blue Hexagon will send findings such as the one below to Security Hub:
Related content
Blue Hexagon Proprietary